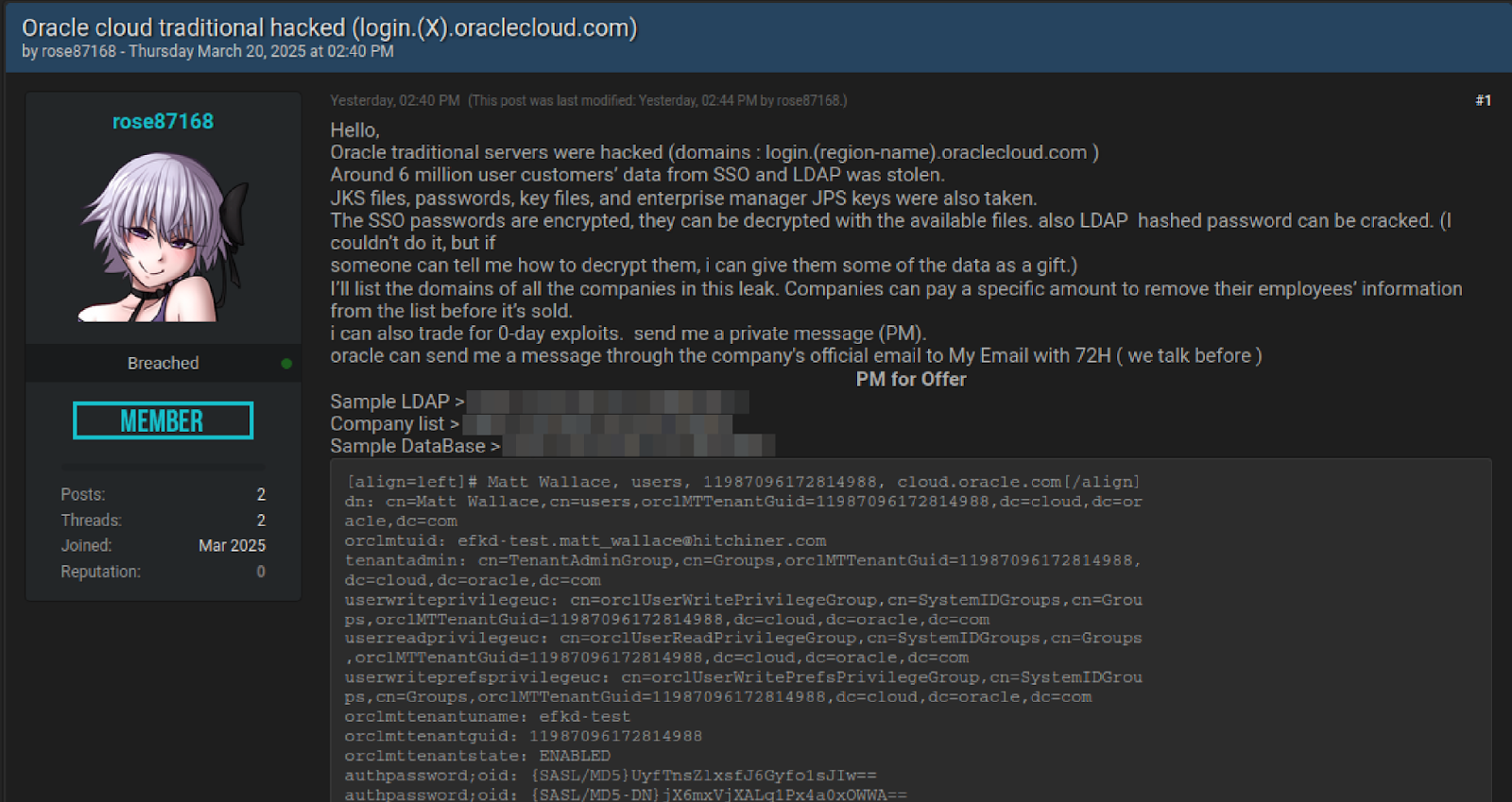
Somebody is claiming to have exfiltrated 6 million lines of data with Oracle Cloud’s SSO and LDAP that includes JKS files, encrypted SSO passwords, key files and enterprise manager JPS keys from servers on login.*.oraclecloud.com
-
Somebody is claiming to have exfiltrated 6 million lines of data with Oracle Cloud’s SSO and LDAP that includes JKS files, encrypted SSO passwords, key files and enterprise manager JPS keys from servers on login.*.oraclecloud.com
The poster has no prior reputation, it is unclear if they're LARPing. Some of the sample data does align with prior infostealer logs, I'm told. https://breachforums.st/Thread-SELLING-Oracle-cloud-traditional-hacked-login-X-oraclecloud-com
-
Somebody is claiming to have exfiltrated 6 million lines of data with Oracle Cloud’s SSO and LDAP that includes JKS files, encrypted SSO passwords, key files and enterprise manager JPS keys from servers on login.*.oraclecloud.com
The poster has no prior reputation, it is unclear if they're LARPing. Some of the sample data does align with prior infostealer logs, I'm told. https://breachforums.st/Thread-SELLING-Oracle-cloud-traditional-hacked-login-X-oraclecloud-com
If anybody is interested, the servers they claim they targeted all run Oracle WebLogic and are managed by Oracle as a SaaS service.
-
If anybody is interested, the servers they claim they targeted all run Oracle WebLogic and are managed by Oracle as a SaaS service.
Has anybody else got Oracle to comment on this? No reply to my queries.
-
Has anybody else got Oracle to comment on this? No reply to my queries.
Oracle are denying a breach to @BleepingComputer, but the threat actor has provided an archived URL which suggests they somehow uploaded a file to the Oracle Access Manager (SaaS solution) frontend.
https://web.archive.org/web/20250301161517/http:/login.us2.oraclecloud.com/oamfed/x.txt?x
-
Oracle are denying a breach to @BleepingComputer, but the threat actor has provided an archived URL which suggests they somehow uploaded a file to the Oracle Access Manager (SaaS solution) frontend.
https://web.archive.org/web/20250301161517/http:/login.us2.oraclecloud.com/oamfed/x.txt?x
The Oracle thing keeps getting more strange. The threat actor has supplied an hour long YouTube video, which appears to be taken from an endpoint inside Oracle... in 2019. They've also supplied a dump of data from 2025, to Hudson Rock. https://www.youtube.com/watch?v=375_G9wAffo
-
The Oracle thing keeps getting more strange. The threat actor has supplied an hour long YouTube video, which appears to be taken from an endpoint inside Oracle... in 2019. They've also supplied a dump of data from 2025, to Hudson Rock. https://www.youtube.com/watch?v=375_G9wAffo
If anybody from Oracle follows me, I definitely think the OCI team needs to spin up security incident response on that YouTube video to try to find out what was happening. It looks like it may be a Citrix session recording of a staff member's access in OCI.
-
If anybody from Oracle follows me, I definitely think the OCI team needs to spin up security incident response on that YouTube video to try to find out what was happening. It looks like it may be a Citrix session recording of a staff member's access in OCI.
Hudson Rock are reporting the Oracle Cloud breach claim threat actor has provided 10k records, and they appear genuine according to one of their customers.
It’s unclear to me exactly what is happening with this one as the threat actor doesn’t appear to understand basic English grammar.. but there are signs something has happened at Oracle.
Big problem for Oracle as I’m not sure how plausible denials will be when threat actor, who sounds 12, is dumping data online.
-
Hudson Rock are reporting the Oracle Cloud breach claim threat actor has provided 10k records, and they appear genuine according to one of their customers.
It’s unclear to me exactly what is happening with this one as the threat actor doesn’t appear to understand basic English grammar.. but there are signs something has happened at Oracle.
Big problem for Oracle as I’m not sure how plausible denials will be when threat actor, who sounds 12, is dumping data online.
CloudSEK are doubling down on their Oracle Cloud breach reporting, despite a denial from Oracle: https://cloudsek.com/blog/part-2-validating-the-breach-oracle-cloud-denied-cloudseks-follow-up-analysis
I am still looking into this and will probably do a blog post this week. The threat actor is still dropping files everywhere and they do tend to point to a security incident at Oracle Cloud.
-
CloudSEK are doubling down on their Oracle Cloud breach reporting, despite a denial from Oracle: https://cloudsek.com/blog/part-2-validating-the-breach-oracle-cloud-denied-cloudseks-follow-up-analysis
I am still looking into this and will probably do a blog post this week. The threat actor is still dropping files everywhere and they do tend to point to a security incident at Oracle Cloud.
Bleeping Computer say multiple Oracle customers confirm their customer data has been stolen. Oracle continue to deny there is a problem.
-
Bleeping Computer say multiple Oracle customers confirm their customer data has been stolen. Oracle continue to deny there is a problem.
Also, that YouTube video I linked above has two hours of audio of Oracle employees talking. I haven’t transcribed it yet.
Separately, the threat actor has shared what they claim to be current config files from Oracle Cloud servers with a different reporter.
I’m deliberately staying out of this one for now as I’m trying to finish Assassin’s Creed Shadows first.. but I think Oracle may have a pending PR disaster when the TikTok deal is due to complete.
-
Also, that YouTube video I linked above has two hours of audio of Oracle employees talking. I haven’t transcribed it yet.
Separately, the threat actor has shared what they claim to be current config files from Oracle Cloud servers with a different reporter.
I’m deliberately staying out of this one for now as I’m trying to finish Assassin’s Creed Shadows first.. but I think Oracle may have a pending PR disaster when the TikTok deal is due to complete.
There’s now been a data breach at Oracle Health, which is separate to the ongoing security issue at Oracle Cloud.
Oracle have not commented publicly on the breach, instead telling people to only talk to their CISO by phone, not in writing. They’ve sent out letters without Oracle letterheads, using external lawyers instead.
The behaviour going on at Oracle with cybersecurity is extremely alarming.
-
There’s now been a data breach at Oracle Health, which is separate to the ongoing security issue at Oracle Cloud.
Oracle have not commented publicly on the breach, instead telling people to only talk to their CISO by phone, not in writing. They’ve sent out letters without Oracle letterheads, using external lawyers instead.
The behaviour going on at Oracle with cybersecurity is extremely alarming.
Going back to the Oracle Cloud security incident, the 2019 video posted by the threat actor: https://youtu.be/375_G9wAffo
Now has an audio transcription https://github.com/j-klawson/oracle_breach_2025/blob/main/youtube_video_transcript.txt
(I’ve redacted the root passwords from screenshot)
-
Going back to the Oracle Cloud security incident, the 2019 video posted by the threat actor: https://youtu.be/375_G9wAffo
Now has an audio transcription https://github.com/j-klawson/oracle_breach_2025/blob/main/youtube_video_transcript.txt
(I’ve redacted the root passwords from screenshot)
I can confirm there has definitely been a serious security incident at Oracle's managed cloud service, and they're attempting to wordsmith their way out of it. https://doublepulsar.com/oracle-attempt-to-hide-serious-cybersecurity-incident-from-customers-in-oracle-saas-service-9231c8daff4a
-
I can confirm there has definitely been a serious security incident at Oracle's managed cloud service, and they're attempting to wordsmith their way out of it. https://doublepulsar.com/oracle-attempt-to-hide-serious-cybersecurity-incident-from-customers-in-oracle-saas-service-9231c8daff4a
Oracle have attempted to hide the Oracle Access Manager access, by requesting archive.org exclude the URL.
-
Oracle have attempted to hide the Oracle Access Manager access, by requesting archive.org exclude the URL.
The wordplay here is Oracle Cloud.
Oracle rebadged old Oracle Cloud services to be Oracle Classic. Oracle Classic has the security incident.
They’re denying it on “Oracle Cloud” by using this scope - but it’s their cloud service.
-
The wordplay here is Oracle Cloud.
Oracle rebadged old Oracle Cloud services to be Oracle Classic. Oracle Classic has the security incident.
They’re denying it on “Oracle Cloud” by using this scope - but it’s their cloud service.
Apparently nobody from Oracle thought to exclude this URL as it still works https://web.archive.org/web/20250301161225/https://login.us2.oraclecloud.com/oamfed/x.txt?mail
-
Apparently nobody from Oracle thought to exclude this URL as it still works https://web.archive.org/web/20250301161225/https://login.us2.oraclecloud.com/oamfed/x.txt?mail
Multiple Oracle cloud customers have reached out to me to say Oracle have now confirmed a breach of their services.
They are only doing so verbally, they will not write anything down, so they’re setting up meetings with large customers who query.
-
Multiple Oracle cloud customers have reached out to me to say Oracle have now confirmed a breach of their services.
They are only doing so verbally, they will not write anything down, so they’re setting up meetings with large customers who query.
Oracle Health customers dealing with the breach there of patient PII, if you’ve had a verbal briefing could you please Signal me? GossiTheDog.1337
I’m interested to see if they’ve told you it was in legacy Oracle Classic aka OCI Gen1 environments, like they have with Oracle Cloud customers - I’m trying to line up if the breaches are actually related.
It appears Oracle migrated people off OCI G1 a few years ago, but left the systems on and unpatched with customer data.
-
Oracle Health customers dealing with the breach there of patient PII, if you’ve had a verbal briefing could you please Signal me? GossiTheDog.1337
I’m interested to see if they’ve told you it was in legacy Oracle Classic aka OCI Gen1 environments, like they have with Oracle Cloud customers - I’m trying to line up if the breaches are actually related.
It appears Oracle migrated people off OCI G1 a few years ago, but left the systems on and unpatched with customer data.
Heise has a look at the Oracle security incident. Oracle didn’t return request for comment when asked about Oracle Classic - I understand from multiple large outlets they’ve also declined to comment.
-
Heise has a look at the Oracle security incident. Oracle didn’t return request for comment when asked about Oracle Classic - I understand from multiple large outlets they’ve also declined to comment.
A class action lawsuit has been filed in the US around Oracle failing to publicly disclose a cybersecurity incident at Oracle Health. https://storage.courtlistener.com/recap/gov.uscourts.txwd.1172831612/gov.uscourts.txwd.1172831612.1.0.pdf
-
 S sebastian@social.itu.dk shared this topic
S sebastian@social.itu.dk shared this topic